limit-req
Summary#
Introduction#
limit request rate using the "leaky bucket" method.
Attributes#
| Name | Type | Requirement | Default | Valid | Description |
|---|---|---|---|---|---|
| rate | integer | required | rate > 0 | the specified request rate (number per second) threshold. Requests exceeding this rate (and below burst) will get delayed to conform to the rate. | |
| burst | integer | required | burst >= 0 | the number of excessive requests per second allowed to be delayed. Requests exceeding this hard limit will get rejected immediately. | |
| key | string | required | ["remote_addr", "server_addr", "http_x_real_ip", "http_x_forwarded_for", "consumer_name"] | the user specified key to limit the rate, now accept those as key: "remote_addr"(client's IP), "server_addr"(server's IP), "X-Forwarded-For/X-Real-IP" in request header, "consumer_name"(consumer's username). | |
| rejected_code | integer | optional | 503 | [200,...,599] | The HTTP status code returned when the request exceeds the threshold is rejected. |
| rejected_msg | string | optional | non-empty | The response body returned when the request exceeds the threshold is rejected. | |
| nodelay | boolean | optional | false | If nodelay flag is true, bursted requests will not get delayed | |
| allow_degradation | boolean | optional | false | Whether to enable plugin degradation when the limit-req function is temporarily unavailable. Allow requests to continue when the value is set to true, default false. |
Key can be customized by the user, only need to modify a line of code of the plug-in to complete. It is a security consideration that is not open in the plugin.
Example#
How to enable on the route or service#
Take route as an example (the use of service is the same method), enable the limit-req plugin on the specified route.
curl http://127.0.0.1:9080/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{ "methods": ["GET"], "uri": "/index.html", "plugins": { "limit-req": { "rate": 1, "burst": 2, "rejected_code": 503, "key": "remote_addr" } }, "upstream": { "type": "roundrobin", "nodes": { "39.97.63.215:80": 1 } }}'You also can complete the above operation through the web interface, first add a route, then add limit-req plugin:
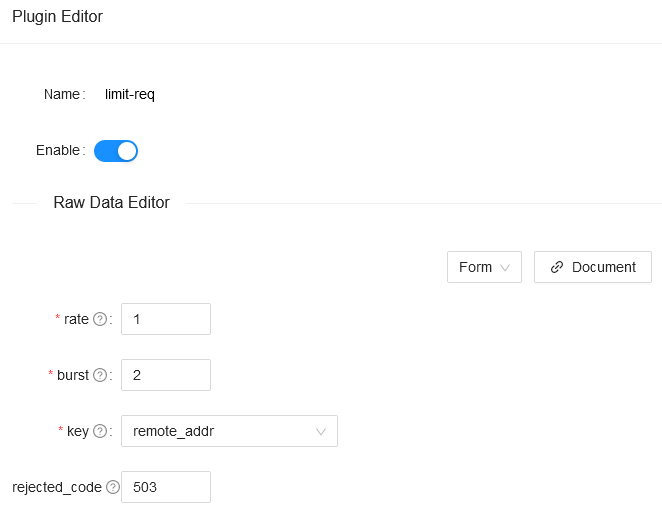
Test Plugin
The above configuration limits the request rate to 1 per second. If it is greater than 1 and less than 3, the delay will be added. If the rate exceeds 3, it will be rejected:
curl -i http://127.0.0.1:9080/index.htmlWhen you exceed, you will receive a response header with a 503 return code:
HTTP/1.1 503 Service Temporarily UnavailableContent-Type: text/htmlContent-Length: 194Connection: keep-aliveServer: APISIX web server
<html><head><title>503 Service Temporarily Unavailable</title></head><body><center><h1>503 Service Temporarily Unavailable</h1></center><hr><center>openresty</center></body></html>At the same time, you set the property rejected_msg to "Requests are too frequent, please try again later." , when you exceed, you will receive a response body like below:
HTTP/1.1 503 Service Temporarily UnavailableContent-Type: text/htmlContent-Length: 194Connection: keep-aliveServer: APISIX web server
{"error_msg":"Requests are too frequent, please try again later."}This means that the limit req plugin is in effect.
How to enable on the consumer#
To enable the limit-req plugin on the consumer, it needs to be used together with the authorization plugin. Here, the key-auth authorization plugin is taken as an example.
- Bind the
limit-reqplugin to the consumer
curl http://127.0.0.1:9080/apisix/admin/consumers -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{ "username": "consumer_jack", "plugins": { "key-auth": { "key": "auth-jack" }, "limit-req": { "rate": 1, "burst": 1, "rejected_code": 403, "key": "consumer_name" } }}'- Create a
routeand enable thekey-authplugin
curl http://127.0.0.1:9080/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{ "methods": ["GET"], "uri": "/index.html", "plugins": { "key-auth": { "key": "auth-jack" } }, "upstream": { "type": "roundrobin", "nodes": { "127.0.0.1:1980": 1 } }}'Test Plugin
The value of rate + burst is not exceeded.
curl -i http://127.0.0.1:9080/index.html -H 'apikey: auth-jack'HTTP/1.1 200 OK......When the value of rate + burst is exceeded.
curl -i http://127.0.0.1:9080/index.html -H 'apikey: auth-jack'HTTP/1.1 403 Forbidden.....<html><head><title>403 Forbidden</title></head><body><center><h1>403 Forbidden</h1></center><hr><center>openresty</center></body></html>Explains that the limit-req plugin tied to consumer has taken effect.
Disable Plugin#
When you want to disable the limit req plugin, it is very simple, you can delete the corresponding json configuration in the plugin configuration, no need to restart the service, it will take effect immediately:
curl http://127.0.0.1:9080/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{ "methods": ["GET"], "uri": "/index.html", "id": 1, "plugins": { }, "upstream": { "type": "roundrobin", "nodes": { "39.97.63.215:80": 1 } }}'Remove the limit-req plugin on consumer.
curl http://127.0.0.1:9080/apisix/admin/consumers -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{ "username": "consumer_jack", "plugins": { "key-auth": { "key": "auth-jack" } }}'The limit req plugin has been disabled now. It works for other plugins.